Proxmox on a server from STRATO
Firewall for the Proxmox STRATO server
This page is about the firewall setting for the Proxmox server before it can be moved to the STRATO server. This is about increasing security when you use Proxmox on a server that is on the Internet.
This is not about the firewall of the virtual guests, but about the Proxmox host itself. In the previous pages, the Proxmox was installed in a virtual machine at home for image preparation. The network was then copied from the STRATO server
and the SSH access was changed. By changing the SSH port and using public key authentication, a lot has happened to the security of the server. But the port of the web interface is still open to the world. And the Proxmox also contains a
few services that work in the background. These should not simply be open to the Internet. Therefore, these ports should now be blocked for the Internet. The web interface is accessed via SSH port forwarding, which was created in Chapter 2.
The port for the SSH server must remain open, which is why increasing security was very important.
Open ports of the Proxmox
The Proxmox consists of a number of services that are there to enable functions of the Proxmox. Obvious is the port required for the web interface. Port 8006 is responsible for this. The web interface is only protected with a user and
password input. You can also turn on two-factor authentication, but it is still not recommended to have this port open. Proxmox also uses this port to communicate with other services. Some other services run with Proxmox to enable
additional functions. There are services that are required for Proxmox's cluster function. If you want to use them on the server on the Internet, these ports must remain accessible. There are services such as VNC or SPICE to control VMs.
You may also want to use these from home if you have VMs running. However, these ports should not be available online to everyone 24/7. Since it is possible to route these ports through the SSH tunnel, you should close them to the Internet
in the firewall and only access them through the SSH tunnel.
The Proxmox developers have an article about the firewall in Proxmox, which also lists at the bottom which services are running and which ports are open. The page for this can be found here.
Why install a own firewall
The Proxmox has a firewall. These can be used for the guests and also set for the host. However, a separate firewall should now be installed and used here. There's a reason for that.
The Proxmox firewall does not block certain ports, even if you set it. This is what it says in the firewall article from Proxmox. But this is not good idea because of the ports mentioned above and the use on a server on the Internet.
Proxmox will not block the ports because the services have to communicate with each other. This is necessary for their function and interaction. Furthermore it is necessary, if you want to use Proxmox's cluster function for example, that
more than one service can be accessed externally. Therefore, the ports would unfortunately have to be opened in this case. You should consider whether you want to have and use these functions for a server on the Internet. In the setup here,
such functions are not used and therefore these ports and all other Proxmox ports are blocked for access from Internet. However, access to the ports remains possible internally on the server and from the virtual networks.
Since Proxmox's own firewall unfortunately refuses to block the ports, you have to install and use your own firewall for this. The classic recommendation under Linux is “iptables”, which is also required for port forwarding to
guests. Since the commands for "iptables" are not that common, there is a frontend for it that can manage the simpler rules required here.
Install UFW and configure
UFW is used and installed as the firewall frontend here. It is a small command line tool that sets "iptables" rules for the user, which are named in the simplified form of UFW. Frontend here means that it is a tool for the command
line that turns its own rules into “iptables” rules.
To be able to use the UFW, you log in to Proxmox. This can also happen here via SSH, as the port for SSH is still permitted (the port from Chapter 02 is used). You should not open and use a Proxmox Host command line in the web interface, as
external access to port 8006 is blocked if the firewall is activated.
If you are on the Proxmox command line, install the firewall using apt install ufw. This is not yet activated after installation, so the ports can be configured at first. This is also better for the SSH
connection because you first have to create the rules that allow the SSH connection before you activate the firewall.
Adding rules to UFW for the Proxmox
After installation, rules are now created for the open ports of Proxmox. There are a few things to consider. In general, rules are now created that prohibit access to the ports from the Internet. This now has to happen from the perspective
of the server at STRATO, even though Proxmox is currently still running in the VM at home. This is because once Proxmox has been installed on the server at STRATO, these rules should apply immediately. Therefore, access to the IP of the
STRATO server should be prohibited here. It makes sense to do the same thing to the IP of the VM. This way you can test everything. Certain ports are then permitted from the “localhost” while inaccessible from the
Internet.
Now below is a command set for the UFW, which sets the rules. In general, “routed” and “incoming” traffic is initially permitted. This means that other ports that are not prohibited by the rules here continue to
work. This allows the SSH port from Chapter 02 and port forwarding for virtual guests which can be configured later. As explained, virtual guests are protected on a private network. This means that other ports (e.g. the SSH ports of a
guest) are safe from the Internet until they are forwarded by the host. The UFW Firewall will never restrict these ports. You can still use the PVE firewall.
Some Proxmox ports, such as the one from the "corosync" service or the one for live migration, are not blocked here. These require services that are not installed and activated when Proxmox was freshly installed.
If the rules shown below are entered, the output of the rules via ufw status verbose should look as shown in the image.
ufw logging off
ufw default allow routed
ufw default allow incoming
ufw allow from 127.0.0.1 to 127.0.0.1 port 8006
ufw deny to 192.168.55.4 port 8006
ufw deny to 85.214.5.42 port 8006
ufw allow from 127.0.0.1 to 127.0.0.1 port 3128
ufw deny to 192.168.55.4 port 3128
ufw deny to 85.214.5.42 port 3128
ufw deny to 192.168.55.4 port 111
ufw deny to 85.214.5.42 port 111
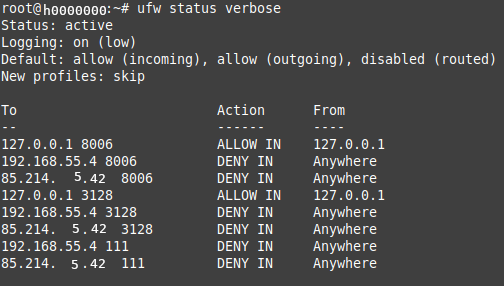
Output of the UFW rules on the terminal (data changed for demo use)
Activating the firewall
If the settings shown above have been set, the firewall can be activated. The firewall is turned on with the ufw enable command. If connections (e.g. web interface on port 8006) have been established to the
Proxmox IP address up to this point, these will now be disconnected. This shouldn't affect the SSH connection. If port 8006 was set as port forwarding via the SSH connection (see Chapter 02), it is now only possible to get access to the web
interface of the Proxmox after establishing the SSH connection and calling "https://<IP-VM-Host>:8006". With these settings the Proxmox can be operated on the Internet.
If something goes wrong with the setting, the firewall can be deactivated again on the VM screen by entering the command ufw disable. If the firewall is successfully activated, the settings shown above apply
automatically every time you restart. This is also different from the base firewall "iptables".